
Stolen or weak passwords are a common cause of data breaches. Businesses can address this risk factor through security awareness training that teaches users best password practices – such as setting strong passwords, changing them routinely, not using the same ones across multiple accounts, and using a password manager.
However, as hackers continue to develop new tactics and create new types of malware, passwords simply aren't enough anymore to safeguard sensitive data. You can greatly reduce your security risk level by adding another layer of protection: Two-factor authentication.
How Two-Factor Authentication Protects Your Data
Two-factor authentication – also called 2FA and multi-factor authentication – is exactly what it sounds like: A security tool that requires users to provide two pieces of information to prove their identity before accessing their account.
This adds an extra step to the logging in process beyond single-factor authentication, which involves simply supplying your username and password. Many 2FA solutions ask you to input a code that you receive through text or via an app on your smartphone. These codes are temporary and are typically only valid for a brief period of time (e.g., 30 seconds).
Why Every Business Should Use 2FA
Given how costly a data breach could be for your organization in terms of clean up, reputation damage and other negative effects, it makes sense to present hackers trying to gain unauthorized access to accounts with another hurdle beyond just stealing or guessing the password.
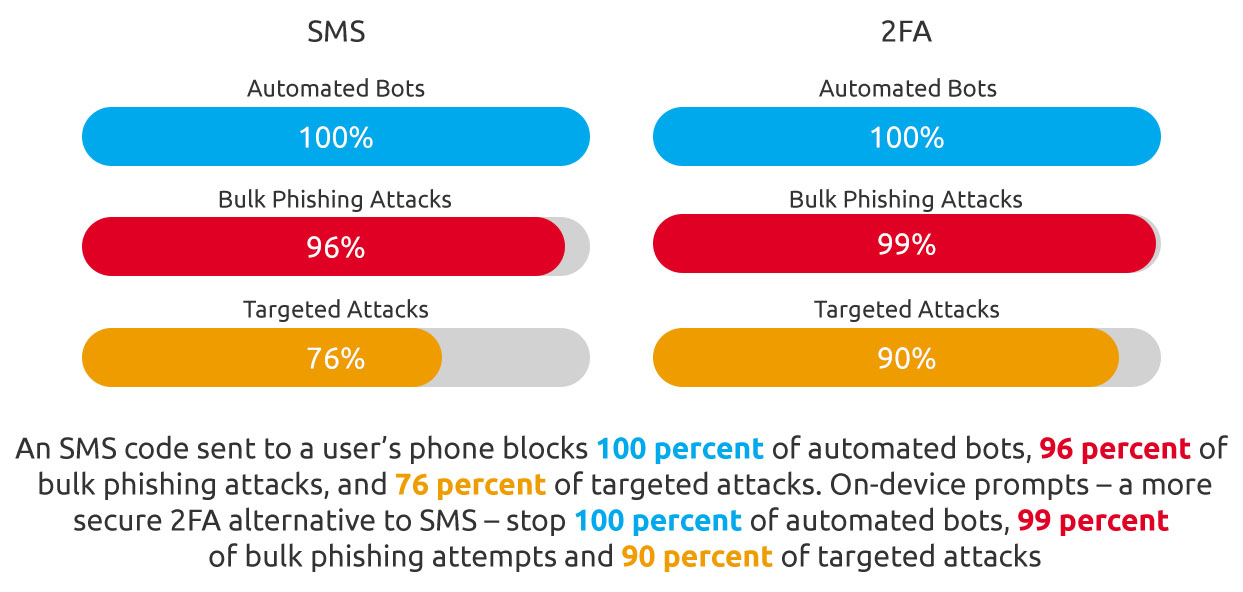
2FA can be the difference between a successful cyberattack and a thwarted hacking attempt. Google has conducted research on this type of security measure and found that an SMS code sent to the user's phone blocks 76 percent of targeted attacks, 96 percent of bulk phishing attacks, and 100 percent of automated bots. On-device prompts performed even better than SMS, blocking 90 percent of targeted attacks, 99 percent of bulk phishing attempts, and 100 percent of automated bots.
Types of Two-Factor Authentication Available
There are several different kinds of 2FA solutions out there. The right choice for your organization depends on which apps you use and what multi-factor authentication methods those programs support.
Most businesses choose one of the following:
- Codes sent via text message: This is the most common 2FA solution and the simplest, since users just need phones that can receive texts. These codes are valid for a limited amount of time after they are issued (e.g., 30 minutes). However, since SMS messages aren't encrypted, leaks are possible. Additionally, cybercriminals can exploit vulnerabilities in phone networks to get access to these codes.
- Codes delivered by authenticator apps: Users must install an app on their smartphones that generates temporary codes for this method. The app will only display the code for a brief time (30 seconds) before generating a new one. This is more secure than relaying codes via text, since the apps use an HTTPS connection. Hackers can only get around this type of 2FA by installing malware on your phone or stealing the actual device.
Don't Leave Your Data Vulnerable to Hackers. Get 2FA Today.
If you'd like to implement two-factor authentication for your organization, our team of security experts can help you find a best-in-class solution that fits your business's specific requirements. Learn more by calling 877-599-3999 or emailing sales@stratospherenetworks.com.