IT security is still a big concern for businesses across all industries as hackers continue to develop new strategies for carrying out cyberattacks. Recently, distributed denial of service (DDoS) attacks have made headlines. On February 28, GitHub.com was unavailable as the result of a DDoS attack that flooded the developer platform with 1.35 terabits per second of traffic – the biggest DDoS incident recorded so far, according to Wired.
After hearing about the GitHub attack, you might be wondering if you should be worried about hackers targeting your organization using a similar method. These FAQs can help you gain a better understanding of this type of cyberattack and learn how to lower your risk of becoming a target.
1. What is a DDoS attack? A DDoS attack involves bombarding a server with data requests from numerous compromised systems, according to Cisco. The goal is to crash the server and the target’s system so that they’re not able to provide services/do business.
There are a number of reasons why hackers might carry out a DDoS attack against an organization. They might have political motivations or plan to extort money from the target, Cisco explains. Additionally, the hackers might work for a rival business that wants to take out the competition.
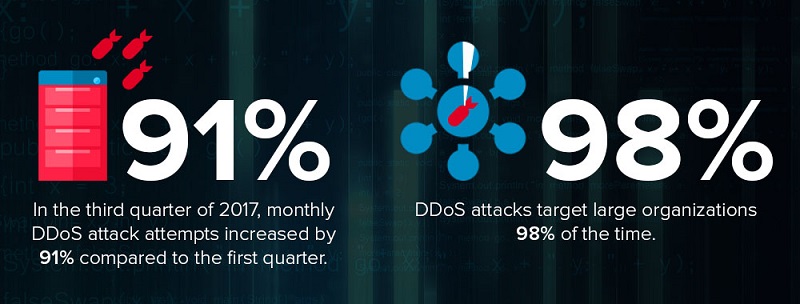
Although DDoS attacks have been around for a while, they’ve become more common and sophisticated in recent years due to the rise of the cloud, Internet of Things, and other advancements in Internet connections, according to a 2017 report from Corero Network Security. In the third quarter of 2017, the report states monthly DDoS attack attempts increased by 91% compared to the first quarter.
2. Why was the GitHub attack a big deal? The digital assault on GitHub was not only the largest DDoS attack recorded so far but also exemplified a different denial of service technique, according to the security news source CSO.
DDoS attacks typically use “botnets,” or networks of hacked computers and other devices that cybercriminals can leverage as an army of “zombie machines,” according to Kapersky Lab. Hackers can create, buy, and/or rent botnets to perpetrate DDoS attacks as well as other types of cyberattacks.
The GitHub attack didn’t use a botnet. Instead, the cybercriminals behind the incident exploited servers that use the Memcached memory caching system, according to CSO. Servers running Memcached are supposed to be protected and part of internal networks, so the system doesn’t have strong defenses against hackers looking to spoof IP addresses and get servers to send out large amounts of data as part of a DDoS attack. However, thousands of Memcached servers are exposed to the open Internet and have as a result become tools for cybercriminals.
3. Should I be worried about hackers targeting my organization with DDoS attacks? DDoS attacks target large organizations 98% of the time, according to Verizon’s 2017 Data Breach Investigations Report. Still, because cybercriminals carry out these types of attacks for various reasons, all organizations of all sizes and across all industries should ensure they have a comprehensive and proactive cybersecurity strategy in place to protect against DDoS attacks and other kinds of cybercrime.
4. How can I protect myself from these types of attacks? As part of your comprehensive IT security policies and solutions, you should have DDoS mitigation services in place to stop any attacks before they start, according to Verizon. It’s also crucial to test them on a regular basis to ensure they actually work. Real-time threat detection, proactive monitoring, and other IT security solutions can help your organization lower its risk of experiencing downtime due to a DDoS attack.
If you’d like to learn more about cybersecurity solutions, feel free to contact our expert team. We work with a wide range of IT security offerings from various providers. Our experience, partner network and vendor agnostic approach allow us to serve as a trusted advisor to businesses seeking solutions that fulfill their unique needs. Feel free to call us at 877-599-3999 or email sales@stratospherenetworks.com.