Note: This blog post was updated on September 8, 2021.
Ensuring your cybersecurity measures are up-to-date and effective is a crucial and ongoing project for any business, regardless of size, location or industry. Cyberattacks continue to occur at a rapid pace: In June 2021, there was 10.7 times more average weekly ransomware activity than the previous year, according to the August 2021 Global Threat Landscape Report from Fortinet.
Identifying vulnerabilities in your IT environment and testing your security posture are both key steps that you should routinely revisit to minimize your organization’s data breach risk. In today’s world of widespread remote work and hybrid workplaces, it’s more important than ever to invest in cybersecurity and check for weak spots in your network. You might have heard the terms “vulnerability assessment” and “penetration test” before while researching cybersecurity solutions. Sometimes, they get used interchangeably, but it’s important to understand that they are distinct tests involving different techniques, goals and results.
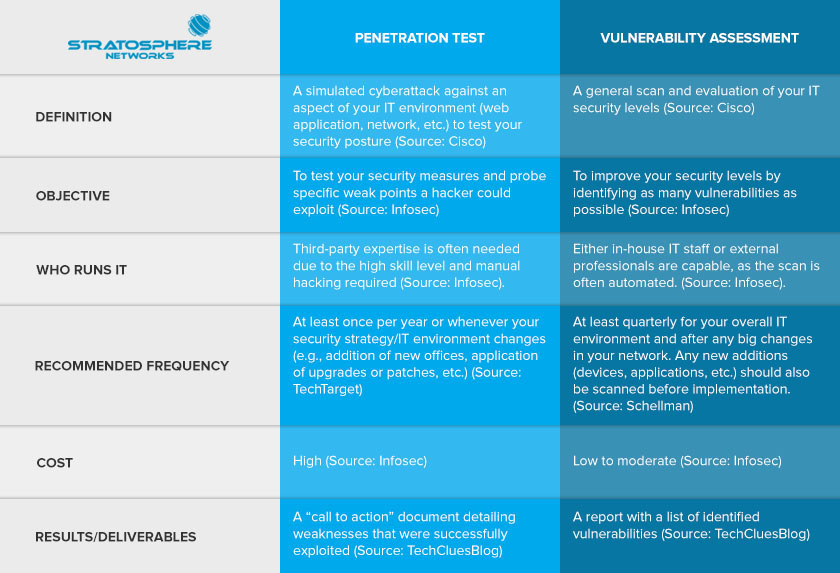
If you’re seeking clarity and would like to understand the distinction between these two cybersecurity tools, the following table explains some of the main ways pen tests and vulnerability assessments differ from one another. Please keep in mind that this isn’t an exhaustive list.
How is a Penetration Test Different from a Vulnerability Assessment?
If you’d like to learn more about pen tests, vulnerability assessments and other cybersecurity solutions, feel free to contact our team of security analysts. Acting to prevent data breaches is vital for all businesses these days, and we can help you build and maintain a comprehensive cybersecurity strategy. As a managed security service provider (MSSP), we can conduct vulnerability scans and pen testing to identify and address any weak points in your network before cybercriminals get the chance to exploit them.
If you’d like to lower your risk level, completing our security risk assessment questionnaire takes just 5 minutes and is a great first step toward better security.
For more information, give us a call at 877-599-3999 or email sales@stratospherenetworks.com.
Sources: